
Is security necessary if you have nothing to hide?
Consider for a moment the very notion of information security. In general, is it really necessary in every aspect of our lives? Do we really need encrypted messaging on our …
Read MoreSecurity For All

Consider for a moment the very notion of information security. In general, is it really necessary in every aspect of our lives? Do we really need encrypted messaging on our …
Read More
Don’t let the constant barrage of vulnerability announcements play with your emotions and drive up your stress levels. Source: Becoming vulnerability agnostic | CSO Online
Read More
Cisco Systems released a patch Monday to fix a critical security vulnerability, with a CVSS rating of 10, in its Secure Sockets Layer VPN solution called Adaptive Security Appliance. Source: …
Read More
Hackers are opportunistic by nature. As device manufacturers continue to add more CPU cores and gigabytes of RAM to smartphones and tablets as well as enterprise… Source: Crypto-Mining: The Next …
Read More
In 2017, we saw digital extortion increasingly become cybercriminals’ first and foremost money-making modus operandi. It’s mostly due to ransomware — cybercriminals’ currently most popular weapon of choice, helping them …
Read More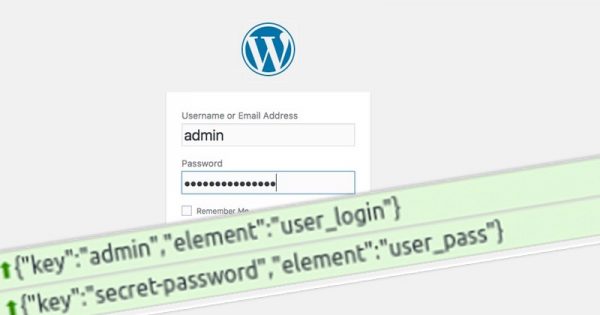
A new report from researchers at Sucuri reveals that websites are once again being found infected by cryptomining code – stealing the resources of visiting computers to mine for the …
Read More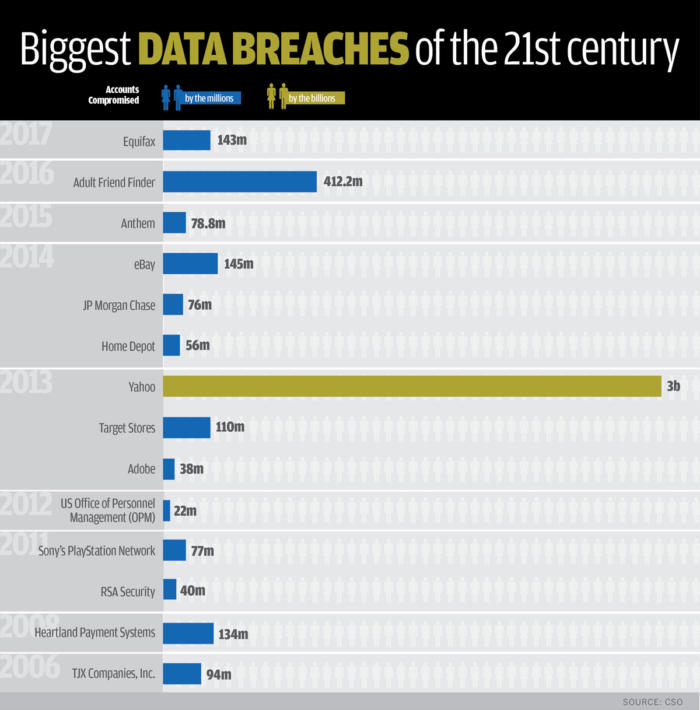
Security practitioners weigh in on the 17 worst data breaches in recent memory. Source: The 17 biggest data breaches of the 21st century | CSO Online CSO’s Taylor Armerding details …
Read More
Consumers are confident they’re safe online, but hackers have proven otherwise, stealing $172 billion from 978 million consumers in 20 countries in the past year. Source: Cybercriminals stole $172 billion …
Read More
Some people aren’t taking hardware vulnerabilities like Meltdown and Spectre seriously. Here’s a point-by-point rebuttal to their arguments. Source: How bad are Meltdown and Spectre? | CSO Online Roger A. …
Read More
The year 2017 was ripe with news of malware, social engineering attacks, and big data breaches. The most infamous of these are the claims of state-sponsored attacks involving Russia’s interference …
Read More