Your company was hacked. Someone other than your employee used their login credentials. Maybe spam was sent out from their email, or logins began appearing from locations the employee has never been. You reset the password, but the lingering question remains in your mind… How did that happen? How did they get “hacked”? Is there malware running rampant, or was the employee just careless?
One of the most common questions I get from users and business owners alike is “how did my account get compromised”? And “Is there anything I can do to prevent it in the future?”
Here is a list of the most common ways accounts can be compromised and used to infiltrate your systems:
10. Failure to patch or update phones, laptops, computers or other systems. When a security update comes out, you should ensure your employees and IT folks apply it immediately because as soon as a patch is released there are teams of malicious actors coordinating around the globe to use that code in the patch to try to create an exploit. Half of the information needed to create an attack for a security vulnerability is in the code released to fix it! You are playing a game of timing with hackers all over the world who have nothing but time, money and resources to create an exploit. Phones can be a big problem because they rely on users to update them. You can encourage users to apply patches by enforcing minimum patch-level requirements for connections to email using Active Sync settings or Mobile Device Management (MDM).
9. Viruses from infected USBs. USB devices are fundamentally broken in their security design, and it isn’t something that can be patched. Malware can still exist on a completely “empty” or “blank” USB simply by including the malware inside the firmware on the USB device itself. Code in the firmware executes instantly when you connect a USB device to a computer. This means an executable program in USB firmware begins running on your computer BEFORE the file can possibly be inspected for infection.
8. Downloading browser plugins, add-ons, and software (usually free). Some software programs that advertise themselves as “anti-malware” are actually malware looking for your credentials (this capability is referred to as key logging, where the program actually logs every keystroke you make). Make sure you train employees to click carefully when downloading software as often boxes are “pre-checked” to add additional items to an installation – we call these PUPs or Potentially Unwanted Programs.
7. Shoulder surfing– this is when someone simply watches a user type a password by looking over their shoulder without a user noticing. Crowded places such as libraries, coffee shops, airports or other public transit stations, where people are often logging into their workplace to compose a few important emails, are ripe for this type of account compromise.
6. Passwords are protected by “challenge questions” which are easily guessed or available through a simple internet search. You know, those questions you get when you type in “I forgot my password”? Have you answered them honestly so you can remember them? That is usually a big mistake. Questions like “What town did you grow up in?”, “What was your high school mascot?”, or “What is/was your mother’s maiden name?” are all EASILY found online for free.
5. Using weak or default passwords. Passwords that are not complex or passwords that contain words easily found in a dictionary are a problem. Though, never changing a default password on a system is even worse.
4. Using unsecured or unencrypted Wi-Fi connections, sometimes called “open” Wi-Fi. This allows malicious individuals to intercept the internet activities of other people. These are common at coffee shops, public transit, airports, etc. This attack is called “man in the middle”. It involves an attacker who relays and sometimes alters the communication between your device and the network or website you’re connecting to.
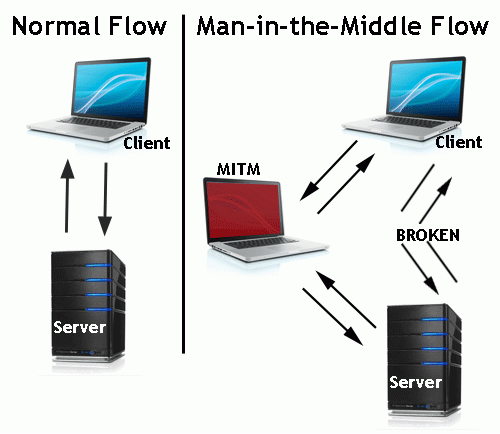
This may seem like a difficult attack to understand, but it is dangerously easily to conduct. The best rule of thumb is that if you are using the same password everyone uses to connect, or there is no password at all, you should not consider anything you’re doing private. For companies, this means that when users authenticate to your websites or to remotely to your company’s own network, the users’ credentials could be compromised.
3. Social engineering – As an attacker, this is the easiest way to “hack” a company or get credentials. Users will always be the weakest point in security, and the only way to combat it is with good user education about social engineering. Social engineering can include an attacker calling or visiting in-person and asking questions. You answer, not realizing how sensitive the information is or believing the attacker to be someone who is authorized to have that info (help desk, your bank, Microsoft etc.). It often uses some common themes that should be taught in awareness education programs. These common tactics include:
- A sense of urgency or time sensitive (act now! Your account will be locked! A package delivery confirmation). This is to make you click or provide information without taking the time to completely think about the authenticity of the caller or email sender.
- Authority claims such as emails claiming to be from the HR Department, the government, the bank, or some law enforcement agency.
- Use of money or intimidation to make people nervous (urgent payment authorization, IRS audit, email from the FBI).
2. Phishing; specifically social engineering via email. Teaching employees simple tricks such as hovering over URL links and reading email headers can be easy ways to educate your users how to avoid social engineering via email. It is possible that phishing maybe the MOST common way your accounts are getting compromised, depending on the education you’ve given to your employees. It is a close tie with #1, password reuse.
1. Password reuse– Your employees use the same password for other things like apps and websites and then THOSE get compromised. App designers do not put user security first, in most cases, so if your employees use the same passwords for personal apps as they use for your company, it is a good vector for compromise. Password reuse is incredibly common. Some studies indicate anywhere between 49% to about 80% of us do it. It is one of the biggest reasons people and their systems get compromised. Both the LinkedIn 2012 and Dropbox breaches were from password reuse.
How do you combat password fatigue that occurs when a single person has to remember too many passwords? Do your homework, and then consider a password management tool such as LastPass or KeyPass. Yes, all your passwords are in one place which some security professionals will say is a vulnerability, but if the choice is between the same password for all your websites and systems and using a password manager? No contest. These companies have an invested interest in keeping your passwords safe, since that is literally their entire business. However, a website for coupon codes has no such financial incentive to keep your password safe.
The key to limiting the damage an attacker can do is early detection. Make sure someone in your company is regularly checking logs for unusual activity like logins from Nigeria or logins during unusual times of day. You can also sign up for breach notifications from free sources like https://haveibeenpwned.com/ to keep informed.




