(Post 8 of the 12-week Information Security Management blog series)
Starting and managing a cybersecurity program can seem incredibly confusing and even overwhelming. Wading through several hundred pages of guidance and standards can easily leave managers and security professionals feeling lost. How do you decide where to start? How do you organize your security program? What guidance or regulations are you required to apply in your organization? Where are you required to apply regulation and where are you given the leeway to do your own thing?
There are several models, or frameworks that you can use that will guide you through the process. Some companies chose to mimic the security programs used by the U.S. federal government and follow the Risk Management Framework and Security and Privacy Controls for Federal Information Systems and Organizations provided by the National Institute of Standards and Technology (NIST). Unfortunately, many smaller organizations may find difficulty in applying a single security framework to their organization, partly because many of the security models they provide were developed with larger, more technologically sophisticated organizations in mind.
Fortunately, there is a framework that scales well to any organization. To fulfil President Obama’s Executive Order 13636 that sanctioned the development of a voluntary model to improve security in critical infrastructure, NIST partnered with private industry information security professionals to develop the Framework for Improving Critical Infrastructure Cybersecurity, also called the “Cybersecurity Framework”. It is intended to be a simple-to-follow scaffolding that can help any organization, of any size, in any industry, and with any level of technological sophistication, plan and manage their cybersecurity program.
The NIST Cybersecurity Framework, unlike most information security documents, is relatively easy to read. It simply aligns policy, business functions, and technology with managing risk. The model is broken into five basic functions, that are essentially actions of a cybersecurity program. Each of the five functions can be then related to tasks or goals that NIST calls “categories”. The categories can then be aligned with specific protective measures (labeled “subcategories”) and a reference describing the measure, such as NIST, ISO, HIPAA, or PCI DSS policies and guidance. Each protective measure can be hand-picked from a different source or even from multiple sources as the organization desires or as legal requirements demand.
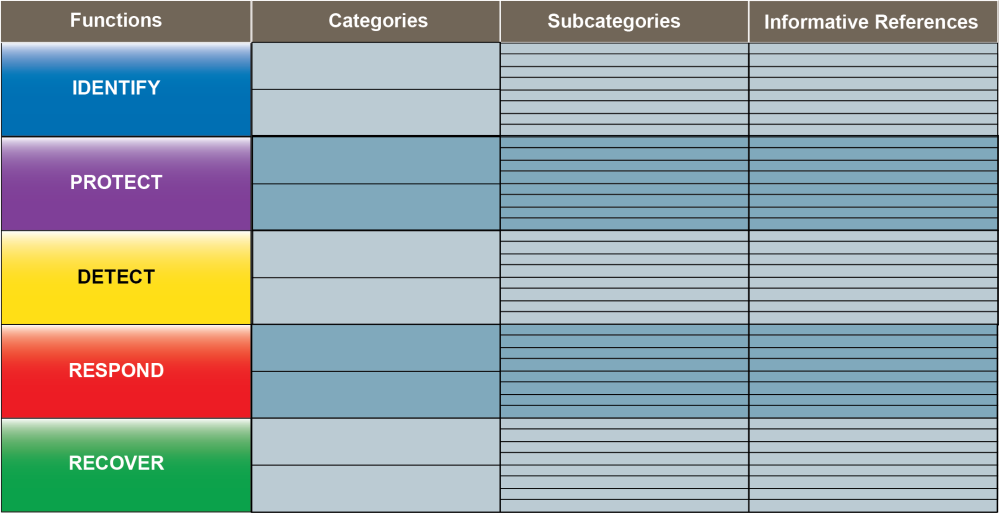
Here is a basic example of some essential goals and activities (categories) that fall under the various functions:
- Identify – Asset management, business environment, applicable governance, risk assessment, and risk management strategy.
- Protect – Control access, train users, implement data security, develop security-centric processes and procedures, and perform maintenance.
- Detect – Identify events and anomalies, perform continuous monitoring, and identify and develop a detection processes.
- Respond – Incident response planning, reestablish communications, perform incident analysis, identify mitigations, and identify security improvements.
- Recover – Develop business continuity and disaster recovery plans, implement security improvements, restore and maintain communications.
By utilizing the Cybersecurity Framework, an organization can plan, implement, and maintain a functional and relatively effective information security program. The framework provides an organized method of collecting all the essential elements of a security program into a single planning document. The document can be reviewed and updated as required. This document can be used as both a plan and a checklist for identifying, implementing, and validating each protective measure listed within it.
Adding even more value, NIST includes links to several valuable resources to help you identify standards, controls, and best practices that you can choose to incorporate in your Cybersecurity Framework plan. The entire NIST document is only 41 pages long, including title page, table of contents, references, a glossary, and several pictures and diagrams (because who doesn’t enjoy pictures and diagrams).




